Note: This blog was updated on October 7 to reflect that only Ivanov, not the affiliated service Universal Anonymous Payment System (UAPS), was the target of the designation.
On September 26, 2024, the U.S. Department of the Treasury’s Office of Foreign Assets Control (OFAC) designated Russia-based exchange Cryptex and Sergey Sergeevich Ivanov (a.k.a. UAPS a.k.a. TALEON), who facilitated laundering for fraud shops, ransomware payments, darknet markets, and other criminal actors. Additionally, Treasury’s Financial Crimes Enforcement Network (FinCEN) has named PM2BTC, a no KYC exchange that has processed over $1 billion and is associated with Ivanov, a “primary money laundering concern” under section 9714(a) of the Combating Russian Money Laundering Act. The action against PM2BTC is the second use by FinCEN of 9714(a) involving cryptocurrency-affiliated entities, following the first such action against Bitzlato in January 2023. Today marks one of OFAC’s largest-ever service-level crypto designations; Cryptex has processed over $5.88 billion worth of transactions since its inception in 2018.
This designation coincides with multiple Dutch and U.S. law enforcement actions that seized the services’ domains, servers, and other infrastructure. The Financial and Tax Crime Investigation Services (FIOD) and National High Tech Crime Unit (NHCTU) of the Netherlands, with assistance from Chainalysis and Tether, seized €7M worth of funds. Concurrently, the U.S. Department of State has issued a reward offering up to $10 million through its Transnational Organized Crime Rewards Program for information leading to Ivanov’s arrest and/or conviction. In addition, according to the designation, the U.S. Secret Service and the U.S. Attorney’s Office for the Eastern District of Virginia are unsealing an indictment of Ivanov and another Russian national, Timur Shakhmametov. These concurrent efforts are part of Operation Endgame, a multilateral, coordinated cyber operation between U.S. and European authorities focusing on dismantling financial enablers of transnational cybercrime.

While UAPS was included as an alias for Ivanov in OFAC’s designation, “Universal Anonymous Payment System” (UAPS for short) is also a payment processor for various fraud shops. This service was allegedly created and/or operated by Ivanov, and on-chain analysis indicates close association between UAPS, Cryptex, and Btc2pm.me. Although Chainalysis has concluded that only Ivanov, not the affiliated service UAPS, was the target of the designation, we recommend that customers take a risk-based approach in assessing their exposure to this service and other entities, according to their respective policies.
Services like Cryptex, UAPS, and PM2BTC are essential facilitators of cybercrime, as they process payments and launder proceeds from the sale of stolen data and personally identifiable information (PII). Criminals typically use this information to orchestrate various scams, identity theft, and account takeovers.
Below, we’ll take a closer look at Cryptex, UAPS and PM2BTC, examining their on-chain activities and role in the cybercrime ecosystem, and how OFAC’s actions are helping drive a global crackdown on fraud.
What is Cryptex?
Cryptex is a Russian-language, instant exchange service that operates a trading platform and an exchange platform.

In January 2022, Cryptex launched CryptexPay to support payment processing in Bitcoin (BTC) and Litecoin (LTC) for online businesses using its platforms, especially those classified as high-risk. CryptexPay further attracted criminals by explicitly advertising its lack of adherence to AML/KYC requirements.
What is UAPS?
UAPS, which stands for Universal Anonymous Payment System, facilitates payments for fraud shops, including the now-designated Genesis Market, BriansClub/Brian Dumps, and Faceless. The project was officially launched in a dark web forum in 2013 as an invite-only underground payment processor. An attractive feature of the service was that its payment processing capabilities could be integrated via API. Per the service terms, merchants are only approved if they receive an invite from another member or permission from the admin. For this reason, it has been very popular for criminals using crypto to finance their activities.
In 2015, many fraud shops transitioned from UAPS to PinPays, a now-defunct version of UAPS that had logo presence on the vendor websites using the service. Some fraud shops even started redirecting users to a PinPays merchant page. Based on the heavy overlap in fraud shop customers and shared wallet infrastructure that is apparent on-chain, it is evident that PinPays was an attempt at an overt rebranding of UAPS. UAPS also shared wallet infrastructure with the no KYC exchange PM2BTC. However in recent years, the exchange function of the service has been minimal, and on-chain behavior indicates that UAPS primarily serves as a fraud-related payment processor.
What is PM2BTC?
PM2BTC is a no KYC exchange that has been operational since 2014 and is closely associated with Ivanov (a.k.a. UAPS). Similar to UAPS and Cryptex, the service facilitated activity on behalf of ransomware actors, fraud shops, and sanctions evasion networks. Today’s Treasury press release highlighted that nearly half of all PM2BTC funds involved clearly illicit sources.
On-chain activity of Cryptex, UAPS and PM2BTC
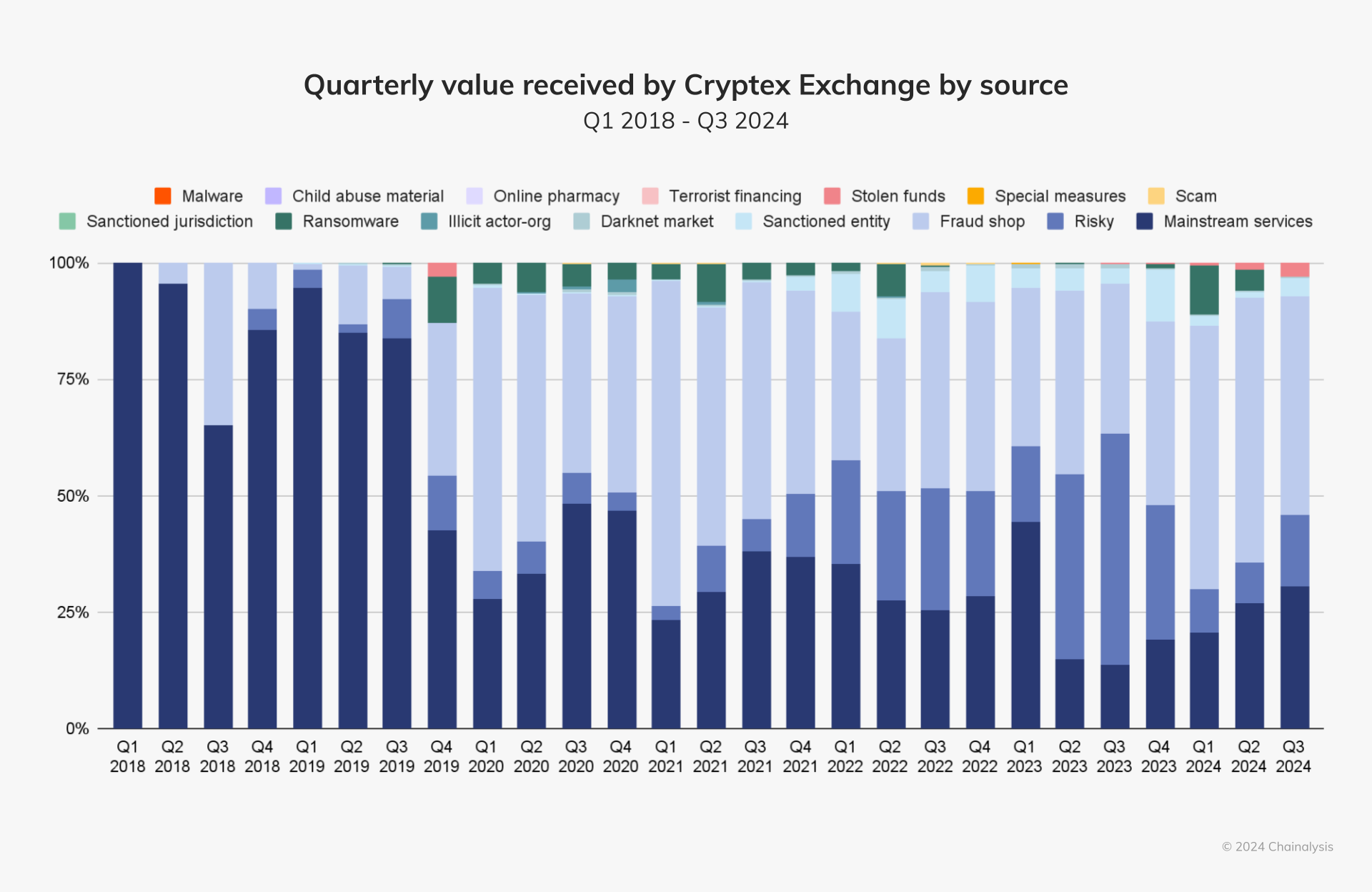
Cryptex has processed over $5.88 billion worth of crypto transactions over its lifetime. Between 2018 and mid-2019, most of its received value came from mainstream services, with some upticks in value received by fraud shops and risky entities. Since the end of 2019, Cryptex has received most of its value from fraud shops, followed by mainstream services, risky entities, and ransomware services.
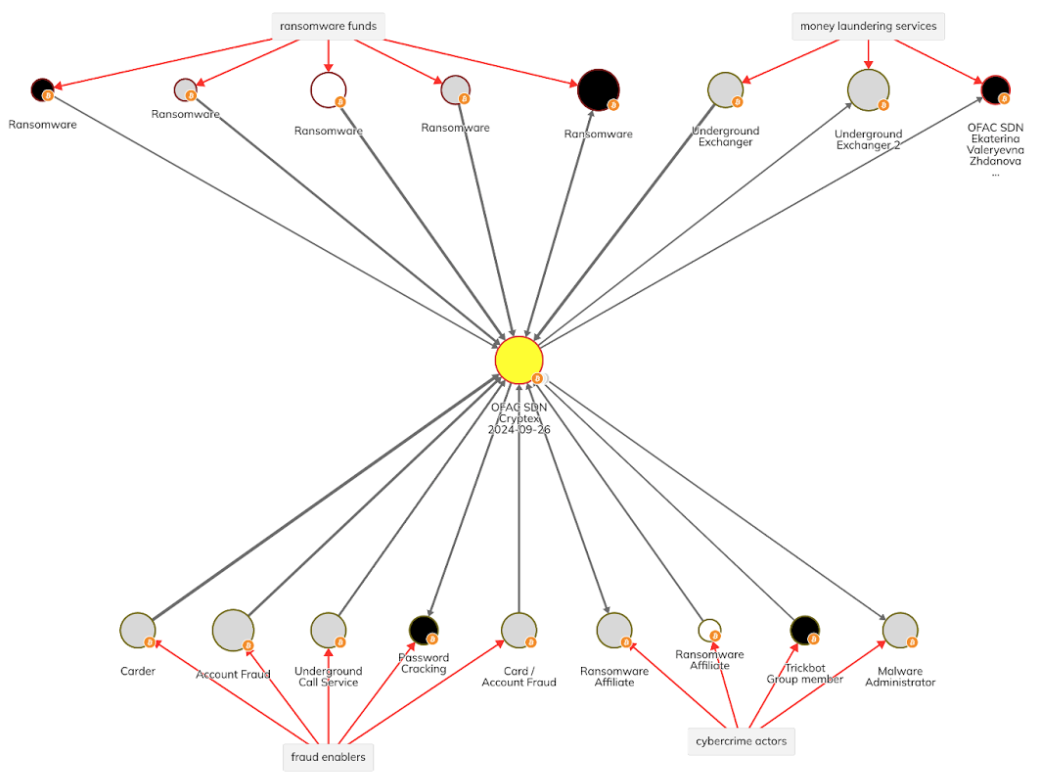
In the below Chainalysis Reactor graph, we see Cryptex’s relationship to a selection of ransomware actors, including underground laundering services, underground call services, and malware-as-a-service providers. Cryptex has processed hundreds of millions of dollars in ransomware proceeds.
We also see Cryptex’s connection to OFAC-sanctioned Russian national, Ekaterina Zhdanova, who used cryptocurrency to launder money on behalf of Russian elites, ransomware groups, and other bad actors.
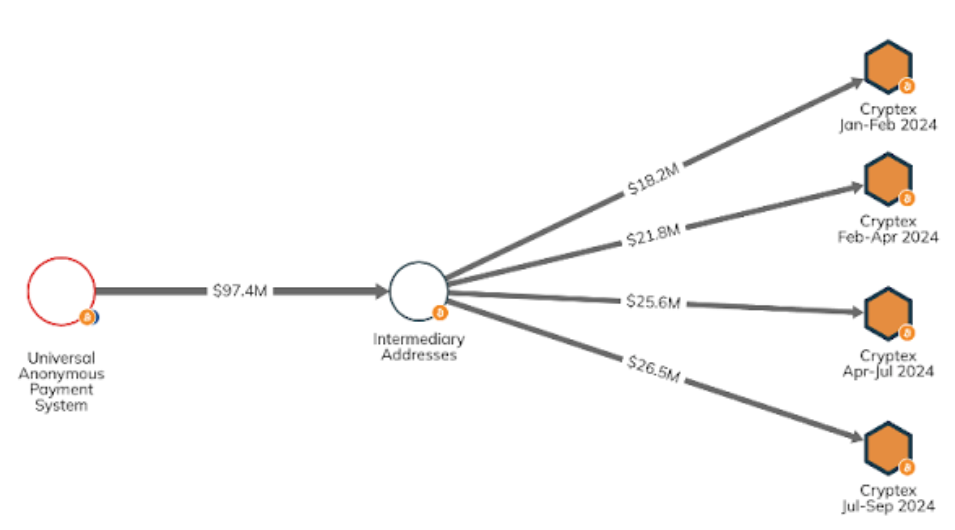
On-chain analysis also reveals the extent of funds processed through Cryptex from UAPS. In 2024 alone, UAPS sent more than $97 million worth of crypto to intermediary addresses, after which funds moved to addresses operated by Cryptex (as seen in the graph below). Of the $97 million, more than $92 million went to four Cryptex addresses.
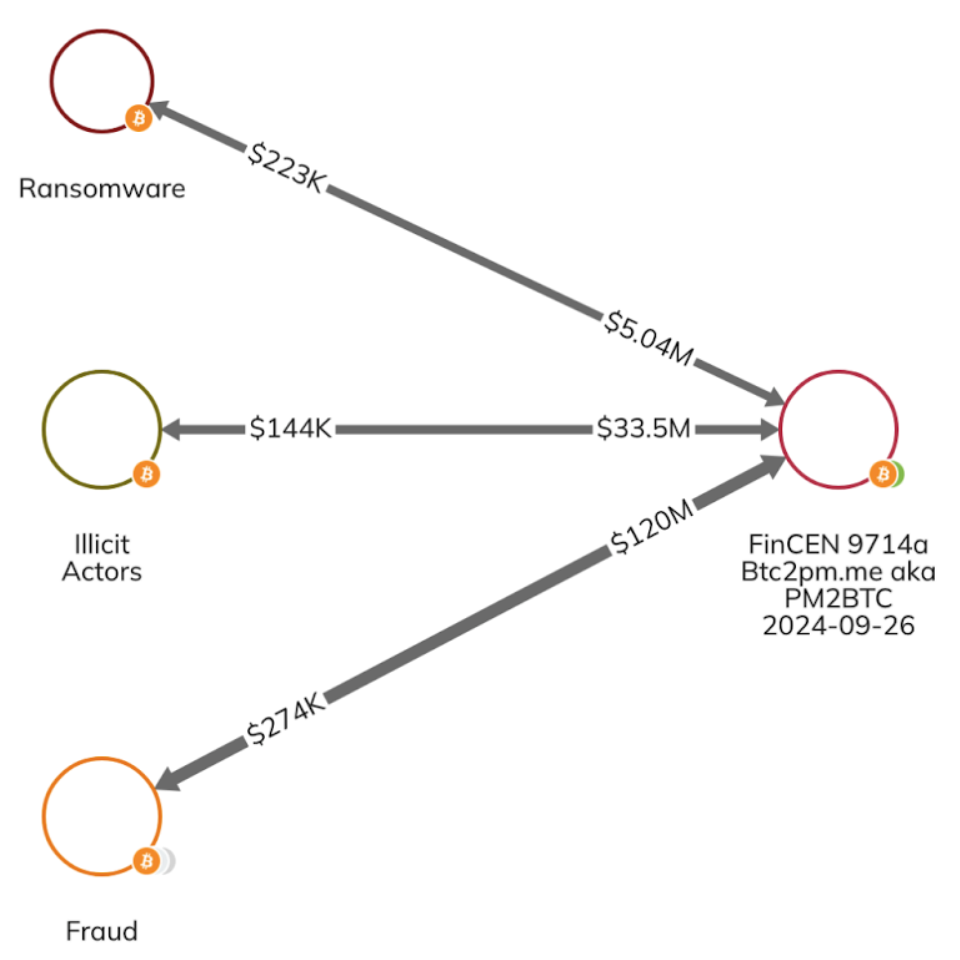
The graph below highlights just a few counterparties of PM2BTC processing hundreds of millions of dollars on behalf of illicit actors, including ransomware and fraud shops.
The global crackdown on fraudulent infrastructure
One of the most critical tactics in disrupting illicit actors is to disrupt the infrastructure they abuse to facilitate money laundering and other transnational cybercrime. Today’s actions represent OFAC’s continued efforts to work with key international partners to make the internet a safer place by shutting down fraudulent services and the infrastructure that hosts them.
We will continue to share any relevant updates on this case when possible.
This website contains links to third-party sites that are not under the control of Chainalysis, Inc. or its affiliates (collectively “Chainalysis”). Access to such information does not imply association with, endorsement of, approval of, or recommendation by Chainalysis of the site or its operators, and Chainalysis is not responsible for the products, services, or other content hosted therein.
This material is for informational purposes only, and is not intended to provide legal, tax, financial, or investment advice. Recipients should consult their own advisors before making these types of decisions. Chainalysis has no responsibility or liability for any decision made or any other acts or omissions in connection with Recipient’s use of this material.
Chainalysis does not guarantee or warrant the accuracy, completeness, timeliness, suitability or validity of the information in this report and will not be responsible for any claim attributable to errors, omissions, or other inaccuracies of any part of such material.

